4 Easy Facts About Sharepoint Data Migration Explained
Display for conformity: Screen the Share, Factor Online atmosphere for conformity with data privacy, security, and administration plans and standards. Assess as well as optimize the search: Review as well as enhance the search capability in Share, Factor Online to make certain that individuals can easily locate and access the migrated data and material - sharepoint data migration. Prepare for mobile gain access to: Plan for mobile accessibility to the moved information and also content, guaranteeing that users can access it from anywhere, anytime, on any type of device.
Prepare for data migration: Strategy for data migration to various other systems or systems as needed, taking into consideration the movement objectives, extent, and requirements. Prepare for ongoing assistance: Prepare for continuous support and maintenance, consisting of updating, patching, and fixing any type of issues that might occur gradually. Guarantee data personal privacy as well as protection: Guarantee that the moved information as well as web content are secured versus unapproved access, violations, and various other security hazards.

Sharepoint Data Migration for Beginners
By maintaining these 25 finest techniques, on your radar, you can ensure that the movement is smooth, effective, as well as straightened with the organization's objectives and also demands, which the moved data and content are protected, easily accessible, and also handled based on ideal methods.
Moving to Share, Point Online can be a complex process and also picking the ideal migration tool is important to make sure a smooth and also effective transition. Below are some suggestions to assist you pick the right device for your Share, Point migration: When comparing Share, Point movement devices like Quest tool, Sharegate tool, Share, Point Migration Device (SMAT), Metalogix Material Matrix, Ave, Factor Migration Tool, as well as Little Bit Titan Migration, Wiz, it is very important to consider factors such as features, ease of usage, supported platforms, performance, and cost.
Criteria, Mission device Sharegate device Share, Factor Movement Tool (SPMT) Metalogix Material Matrix Ave, Factor Movement Tool Bit, Titan Migration, Wiz Kinds, Cloud Base Non-Cloud Base Non-Cloud Base Non-Cloud Base Non-Cloud Base Cloud Base, Meaning, Pursuit tool may refer to numerous products offered by Quest Software program, each with its own set of functions as well as capacities. sharepoint data migration.
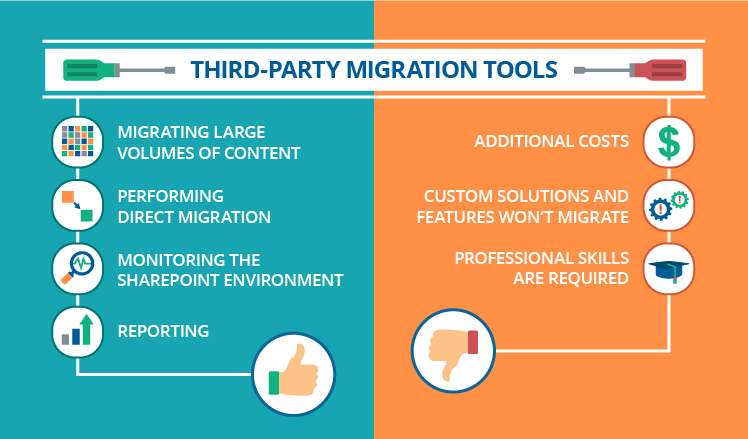
See This Report about Sharepoint Data Migration
Attributes, Supplies automatic evaluation, material mapping, scheduling, as well as supports Supports migration from numerous resources, pre-migration evaluation, material mapping, as well as scheduling. Totally link free migration tool provided by Microsoft, sustains movement from on-premises Share, Factor sites, data shares, and other cloud storage service providers. Gives automated discovery, pre-migration evaluation, metadata mapping, and also granular content movement.
Supports movement from different resources, pre-migration assessment, information mapping, as well as scheduling. Scalability, Deals with large as well as complex migrations effectively. Understood for scalability and managing intricate migrations.
Alleviate of Use Provides an easy to use cloud-based user interface. Provides a straightforward and also instinctive customer interface. Offers an easy to use interface. Offers a comprehensive interface Provides an user-friendly interface. Offers an easy to use cloud-based user interface. Sustained Movement Scenarios Moves from Share, Factor on-premises, documents shares, as well as other collaboration platforms to Share, Factor Online.
Migrates to Share, Aim Online or One, Drive for Organization. Rates: Free to make use of. Migrates from various sources, consisting of Share, Point on-premises, data shares, Exchange Public Folders, and also other partnership platforms to Share, Factor Online. Migrates from numerous resources to Share, Factor Online. Migrates from numerous sources to Share, Point Online.
Our Sharepoint Data Migration Ideas

Constraint It may have restrictions in handling complex migration scenarios and not able to migrate customized checklist like study list. It might have constraints in managing complex movement scenarios as well as modification demands.
There are some limitations on the documents size that can be moved at one shot. At Netwoven, we have actually efficiently performed over 100 of such migration tasks from Google work space, M365, Microsoft On-Prem Framework to M365 spanning over even more than a years in various Tier 1 market sections. Our experience suggests that there is no person tool that fits all.
We have actually been able to establish a set of recyclable devices for material inventory evaluation, movement mapping, movement screening as well as audit. Below is a sample photo of one of our devices that makes it possible for the user to easily flag the migration choices for any material in the source. These tools this hyperlink enhance all the above as well as can show to be handy for any type of migration job taken on (sharepoint data migration).








